Hesam Seyed Mousavi, March 25, 2015
Source: IPCFirmware
In this tutorial we are going to understand the ip camera firmware software like what actually running inside ip camera by doing some reverse engineering on the firmware of ip camera.
For reverse engineering we need to have camera firmware image you can get from you camera vendor website for flush or upgrade the camera firmware.
Camera firmware is nothing but the complied or compressed .bin file for flashing the camera or upgrades the firmware.
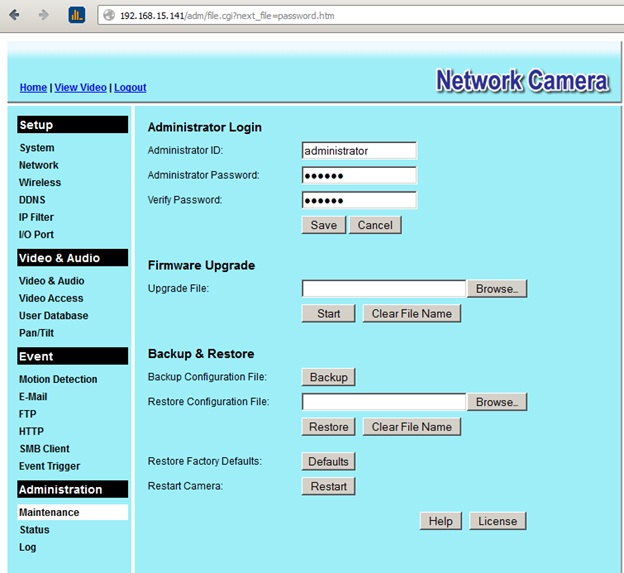
Here the interface of the ip camera so that we can browse the .bin firmware file and upgrade the camera firmware.
But here are not going to upgrade the firmware but reverse engineer it for fun and profit.
Now we need to get the camera firmware from the vendor.
Here the required the bin camera file or firmware.
First we need to analyze that what this file is all about (using Linux file utility)
So using file utility we did not find any interesting thing. Let move further
Now we are going to use hexdump and string utility against the firmware for more information.
So first we need to look at the strings output and analyze it.
Here we can see that firmware is based on LINUX OPERATING SYSTEM for embedded devices. So let also see the hexdump may be it can reveal more interesting things for us.
But looking at the hexdump we didn’t figure out any new interesting things only we can see html and other commands cgi scripts callings.
Now we are going to use binwalk against the firmware image it may give some false result.
It give very useful information like the compressesion method used is gzip and the file system is squashfs little endian version 3 and more interesting information.
Now we know that firmware is based on Linux and the file system is squashfs and the compressed data format is gzip now we are going to use another utility so that we can extract and decompress the data.
Here the firmware has been extracted using the firmware mod kit utility.
Now we can also decompress the data and we find very interesting things inside it (decompression can be done using decompression utility for squashfs system included in firmware mod kit)
Here we can see that the camera firmware is from sercommn (vendor)
Now we can see all the file system inside the firmware image and everything
Here we can see each n every cgi and other files and folder inside the camera’s webserver.
Here is the index html file which is running inside the camera, model is 8061.
So finally you reverse engineered the camera image or firmware hack it according to your own wish (make required manipulation according to need).
Source: IPCFirmware